Are you tired of worrying about the security of your VoIP calls? 📞
If yes ✔️, then you have come to the right place. It’s more important than ever to protect your communications against cyberattacks. you might want to learn some important techniques to safeguard your calls and provide peace of mind.
In this blog, you will learn about VoIP Security, its Types, VOIP security standards, Best Practices, and how to protect your VoIP system from potential dangers with network security and encryption.
🔑Key points
- VoIP security refers to procedures and tools used to keep malicious users and illegal access out of VoIP systems.
- Encryption protocols like TLS and SRTP are crucial for securing VoIP conversations by jumbling data during transmission and encrypting speech material.
- Eavesdropping, Phishing (vishing), Malware and Viruses, DoS and DDoS attacks, and VOMIT pose significant risks to VoIP systems.
- KrispCall offers advanced features to protect against eavesdropping and hacking, real-time threat detection, and user authentication and access control for high-security VoIP communications.
What is VoIP security?
VoIP security refers to the practices and technologies employed to safeguard Voice over Internet Protocol (VoIP) systems from unauthorized access, eavesdropping, and other malicious activities.

VoIP security is crucial for safeguarding voice communications over the internet. VoIP network security is cloud-based and virtualized, setting it apart from typical security systems for legacy PBX (Private Branch Exchange) or other on-premises systems. One of the main distinctions between a VoIP-based phone system and a traditional phone system is this.
Why Is VoIP Security Important?
VoIP Security is important for following reasons:
- Protecting Sensitive Information: VoIP calls are vulnerable to interception because, unlike traditional phone lines, they are sent via the Internet. Hackers may use vulnerabilities in VoIP systems to listen in on conversations, take credit card numbers or other private information, steal sensitive data, and even utilize the information for fraud or identity theft.
- Maintaining Compliance: Regulations such as HIPAA and PCI DSS, which require certain data security procedures, apply to businesses in specific areas, such as healthcare and finance. VoIP system security breaches can result in costly penalties and harm one’s image.
- Ensuring Business Continuity: VoIP phones are frequently necessary for day-to-day operations. VoIP service disruptions due to security breaches can completely stop communication, which affects customer service, revenue, and productivity.
- Preventing Fraud: Fraudsters may attack VoIP systems to take advantage of weaknesses and conduct illegal international calls, incurring costs for the company owner.
What are the VoIP Security Standards?
VoIP security is based on a mix of protocols and industry best practices rather than a single overarching standard. Below is a summary of the essential components:
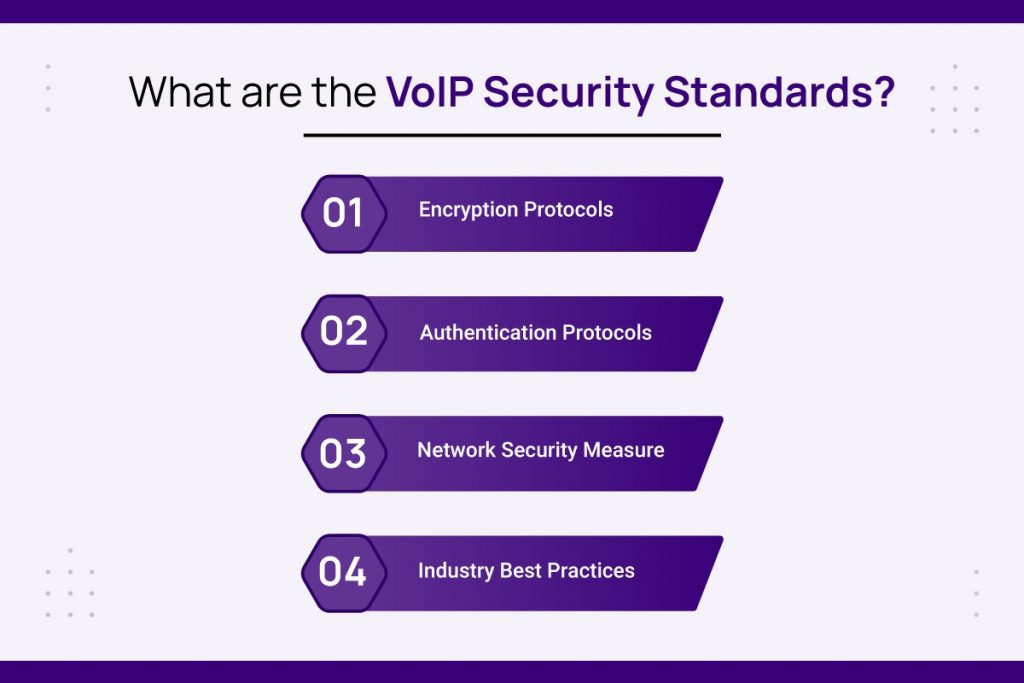
1. Encryption Protocols
Encryption methods that jumble data during transmission are essential to the security of VoIP conversations. The primary two criteria are:
- Information related to caller ID and call routing is encrypted via Transport Layer Security (TLS).
- Make sure the speech material is encrypted using the Real-Time Transport Protocol (SRTP), rendering it unrecognizable to anybody listening in on the conversation.
2. Authentication Protocols
The identities of individuals and devices trying to access the VoIP system are confirmed by the use of these protocols. Passwords, Certificates, and Multi-Factor authentication (MFA) are examples of common techniques.
3. Network Security Measure
The VoIP network itself is secured in part by network segmentation, intrusion detection systems (IDS), and firewalls. To reduce the impact of a breach, these systems segregate VoIP communication from other data, filter traffic, and spot unusual activities.
4. Industry Best Practices
Robust VoIP security requires not just adherence to particular protocols but also recognized best practices, such as strong password restrictions, software updates, and user education on VoIP security red flags.
Types of VoIP Phone Security Issues & Risks and How to Prevent Them
Here are some types of VoIP security issues and risks and how to prevent them:

1. Eavesdropping and Call Tampering
Eavesdropping refers to intentionally listening in secret to someone else’s private conversation. Eavesdropping occurs when a third party intercepts, monitors, or accesses data that is transmitted between two devices.
Risk:
VoIP calls are vulnerable to interception and listening by hackers, who may take advantage of private information or interrupt existing discussions.
Prevention:
Use Secure Real-time Transport Protocol (SRTP) to encrypt voice communications while they are being sent. To provide an extra degree of security, encrypt all internet traffic—including VoIP calls—by using a VPN (Virtual Private Network).
2. Phishing (Vishing)
Phishing is a cyberattack method where scammers attempt to deceive victims into clicking on fraudulent links in emails. Vishing refers to fraudulent phone calls or voice messages designed to trick victims into providing sensitive information, such as login credentials, credit card numbers, or bank details.
Risk:
Calls that are intended to mislead you into disclosing private information, such as credit card numbers or passwords.
Prevention:
Employees should be trained to avoid answering unwanted calls, especially those who ask for personal information. Encourage calling back to confirm the identity of the caller via proper means before disclosing any private information.
3. Malware and Viruses
Malware is an umbrella term that encompasses any harmful program or code designed to target computers, networks, or devices. A virus is a specific type of malware that attaches itself to another program and, when executed, replicates by modifying other computer programs.
Risk:
VoIP systems may become infected with malicious software, which can then interrupt call quality, steal data, or even start more network assaults.
Prevention:
All devices used for VoIP conversations should have anti-virus and anti-malware software installed and kept up to date. Update all software with the most recent security fixes, including the VoIP system itself.
4. Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks
A DoS attack floods a server or network resource with an overwhelming amount of traffic, rendering the targeted service unavailable. A DDoS attack is an amplified version of a DoS attack, leveraging multiple computers or machines to flood a targeted resource.
Risk:
These attacks overwhelm VoIP servers with traffic, making them unavailable for legitimate calls.
Prevention:
Select a VoIP company that has DDoS mitigation techniques and a strong infrastructure. Install firewalls to stop unauthorized access and filter incoming traffic.
5. VOMIT (Voice over Misconfigured Internet Telephony)
VOMIT (Voice over Misconfigured Internet Telephones) is a term that highlights a serious security threat related to VoIP (Voice over Internet Protocol) phone systems by hackers to exploit misconfigured VoIP systems.
Risk:
Using VoIP systems that aren’t configured correctly to turn calls into files that can be sent quickly, perhaps disclosing private information like the source of the call and login credentials.
Prevention:
Ensure proper configuration of your VoIP system, following secure protocols recommended by your provider. Regularly review and audit your VoIP system configuration for any vulnerabilities.
How to Measure VoIP Security?
VoIP security is measured using a multi-layered methodology that evaluates many facets of your system’s overall robustness. The following are some crucial tactics:
1. Self-Assessment
Assess your VoIP provider’s security measures by examining their encryption protocols, network security practices, and adherence to relevant standards such as HIPAA and PCI DSS.
Additionally, review your internal security measures, including strong password policies, user access controls, firewall configurations, and ensuring software is kept up-to-date. Regularly conduct vulnerability scans on your VoIP system and network to pinpoint any potential weaknesses.
2. Penetration Testing
Hire a security expert to carry out penetration testing, which replicates actual attack scenarios, to find weaknesses in your VoIP system. Vulnerabilities in configuration, user access, and network security can be found with this procedure.
3. Monitoring and Logging
Use monitoring tools to keep tabs on VoIP call traffic, spot odd trends, and find any security breaches. Check call logs for any unusual behavior, such as long or undeclared calls, or overseas calls to places of high risk.
4. User Education and Awareness
Train your employees and users on VoIP security best practices, including, Recognizing and preventing phishing attacks. Keeping secure passwords private and keeping them secret from others. Exercising caution when utilizing VoIP on unprotected Wi-Fi networks. The authorities of any questionable activities involving VoIP calls or system access.
5. Third-party Audits
Think about having an established third-party company examine your security protocols and VoIP system. This may provide you with an unbiased evaluation of your security posture and point out areas that need work.
What are the different methods for conducting VoIP security Testing or assessments?
VoIP (Voice over Internet Protocol) security testing is looking at several VoIP system components to find weaknesses and make sure the system is resilient to any attacks.
The following are some typical techniques for carrying out evaluations or tests of VoIP security:
Vulnerability Assessment
This is looking for known vulnerabilities in software, protocols, or settings inside the VoIP infrastructure. VoIP components, including servers, gateways, and endpoints, can be found to have vulnerabilities by using automated vulnerability scanning tools like Nessus, OpenVAS, or Qualys.
Penetration Testing
Perform detailed penetration testing on your VoIP system. To find weaknesses entails replicating actual assaults. List all of the VoIP settings, extensions, and services. Check for common vulnerabilities like unpatched software, weak passwords, and unsafe setups. To evaluate SIP-based VoIP systems, utilize programs such as SIPVicious PRO.
Denial-of-Service (DoS) Testing
DoS attacks have the potential to interfere with VoIP services by flooding servers or network infrastructure with too much data. To evaluate the system’s capacity to manage and mitigate such threats, DoS vulnerabilities are tested by simulating these assaults. For this, one can use tools such as LOIC (Low Orbit Ion Cannon) or specialized DoS testing tools.
Encryption Testing
Sensitive VoIP conversations must be encrypted to prevent eavesdropping and interception. Verifying the robustness and application of encryption techniques (such as TLS for signaling and SRTP for media) to make sure they adhere to security standards is known as encryption testing. This involves evaluating encryption techniques, certificate checking, and key management.
Authentication and Authorization Testing
VoIP systems utilize permission and authentication procedures to manage access and prevent unwanted use. To test these mechanisms and stop unwanted access to VoIP resources, it is necessary to confirm how well user authentication techniques (like passwords and biometrics) and access controls (like role-based access control) work.
What Are Some Best Practices for VoIP Security?

Here are some best practices for ensuring powerful VoIP security:
1. Encryption
VoIP entails encrypting voice data packets while they are sent over networks, such as the Internet. Organizations may guarantee that confidential discussions are kept private and safe from eavesdropping or interception by unauthorized parties by using robust encryption protocols, including Secure Real-Time Transport Protocol (SRTP) or Transport Layer Security (TLS).
2. Network Security
Protecting VoIP systems against several kinds of cyber threats, such as malware, hacking attempts, and denial-of-service (DoS) assaults, requires the implementation of network security measures.
Strong network security tools can help stop unwanted access to VoIP networks and lessen the chance of assaults. Examples of these tools are firewalls, intrusion detection and prevention systems (IDS/IPS), and virtual private networks (VPNs).
3. Access Control
Limiting access to VoIP systems and resources to authorized people or devices is known as access control. This entails putting in place robust authentication procedures, such as passwords, usernames, and biometric authentication, to confirm users’ identities before allowing them access to VoIP services.
Furthermore, people can be granted particular permissions and privileges according to their responsibilities within the company by using role-based access control, or RBAC.
4. Strong Authentication
By requesting numerous kinds of verification from users before granting access to VoIP systems or services, strong authentication techniques like multi-factor authentication (MFA) enhance security. If a user’s password is lost or exploited, this helps prevent unwanted access.
5. Regular Audits and Monitoring
Frequent VoIP system audits and monitoring are essential for quickly identifying and addressing security concerns. Monitoring network traffic, examining system logs, and doing vulnerability assessments are all part of this process to find and fix possible security flaws before attackers can make use of them.
6. Employee Training
Essential elements of a thorough VoIP security plan include employee knowledge and training. Security basic practices, such as making strong passwords, spotting phishing attempts, and reporting unusual activity, should be taught to staff members.
Employees may actively participate in safeguarding company assets by receiving training that enables them to recognize the significance of VoIP security.
What are the Future Trends in VoIP Security?
VoIP’s rise has improved communication simplicity and flexibility but also presented new security risks. Experts believe that as VoIP develops further, the following major themes will influence how people and corporations protect VoIP calls:
Next-Gen Encryption
Even more complex encryption algorithms are anticipated in the future to combine data and render it unreadable to eavesdroppers, but standard encryption techniques are now in use.
Robust Authentication
Multi-factor authentication (MFA), which requires more than just a password but also extra verification processes like fingerprint scans or one-time codes, is probably going to expand even more.
AI-Powered Security
VoIP security is going to become more dependent on artificial intelligence (AI). Artificial intelligence can examine call trends and detect unusual behavior, which might prevent attacks from occurring.
Blockchain Integration
Blockchain technology has a promising future for VoIP security, even though it is still in the exploration stage. By removing a single point of vulnerability, the decentralized structure of blockchain technology may increase the security of VoIP systems against hackers.
Focus on User Education
Since every security mechanism is flawed, user awareness will always be important. More money is anticipated from businesses to teach staff members about VoIP security best practices and how to spot and steer clear of social engineering schemes.
KrispCall: Top Notch High Secured VoIP Phone System
KrispCall is a VoIP phone system that offers advanced features for personal and business use. Instant access to local, toll-free, and vanity phone numbers is available in more than 100 countries.

In addition to integrating with your preferred CRM system, you can track and listen to call records, make instant phone calls or texts, establish a cloud-based multi-location contact center for sales and support, and much more.
Let’s explore how KrispCall can provide security to your VoIP phone system:
1. Secure Voice Transmission
KrispCall uses end-to-end encryption to protect data and ensure that only authorized parties can access and understand the content of the call.
2. Protecting Against Eavesdropping and Hacking
VoIP systems face the risk of eavesdropping attacks; however, KrispCall secures the communication channel to mitigate this risk. By using this method, it successfully prevents illegal access to all content, guaranteeing the security of private data.
3. Real-Time Threat Detection
KrispCall consistently monitors call traffic for any potential threats. If there is any suspicious activity, it takes immediate action.
4. User Authentication and Access Control
Strong user authentication procedures are used by KrispCall to restrict access to only those who are authorized and in possession of valid credentials. To further strengthen security measures, it also employs role-based access control, which restricts privileges depending on certain user responsibilities.
Conclusion
In the current digital environment, protecting your VoIP conversations is essential. Strong security measures must be put in place to safeguard confidential data, guarantee regulatory compliance, preserve business continuity, and stop fraud in light of the growing threat of cyberattacks.
You can strengthen your VoIP system against a variety of security risks by using authentication techniques, encryption protocols, network security measures, and industry best practices.
Think about KrispCall if you’re looking for an excellent, very safe VoIP phone solution. KrispCall offers complete security for your VoIP communications, guaranteeing privacy, confidentiality, and peace of mind.
FAQs
How vulnerable are VoIP cyberattacks?
VoIP systems are vulnerable to a wide range of online threats, including denial-of-service (DoS) assaults, call hijacking, and eavesdropping. However, these threats may be greatly reduced by putting strong security measures in place.
Are there any regulatory compliance requirements for VoIP security?
Yes, to guarantee the secure handling of sensitive data transferred via VoIP, enterprises must abide by regulatory compliance requirements such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA).
What role does encryption play in VoIP security?
Encryption is essential to VoIP security because it encrypts the data being transferred, making it unintelligible to unauthorized interceptors and protecting the integrity and confidentiality of communication channels.
What are the primary security challenges associated with VoIP implementation?
The primary security challenges include securing endpoints, protecting against toll fraud, ensuring data confidentiality, and guarding against unauthorized access to VoIP networks.