Have you ever received a suspicious text message asking for personal information or urging you to click on a link?🤔
If so, you may have encountered a form of cybercrime known as “smishing”. It is a combination of SMS and phishing.
Smishing is a sneaky method where cyber criminals send text messages to trick people and compromise their system security. Unlike phishing, which mainly uses email, smishing uses text messages to pull off scams.
In this comprehensive guide, you will learn about smishing, including how it works, common tactics used by scammers, and most importantly, how to protect🔐yourself from smishing attacks.
🗝️ Key Highlights
- Smishing is a cyber scam where scammers use fake texts to deceive people into sharing sensitive information, downloading malware, or sending money to criminals.
- Examples of Smishing are Customer Support Scams, Fake Job Offers, Government Impersonation, Shipper Impersonation, and Boss/Colleague Scams.
- Smishing attacks exploit trust and vulnerability through deceptive text messages using urgency, rewards, or fear to convince recipients to click malicious links or share personal data.
- You can identify a smishing attack by being cautious of urgent requests, messages asking for personal information or money, unknown senders, grammar/spelling errors, and avoiding storing sensitive data on your phone.
- You can defend against smishing attacks by avoiding clicking suspicious links, verifying message sources before sharing information, reporting suspicious messages to authorities, and many more.
Let’s tackle the Smishing attack.🚀
What is smishing?
Smishing is a social engineering cyber attack in which scammers send fake text messages to trick individuals into giving their sensitive information, downloading malware, or transferring funds to cybercriminals.
Smishing combines SMS (Short Message Service) and Phishing (fraudulent attempts to obtain sensitive personal information).

Just like email-based phishing attempts, SMS phishing messages often appear to come from trusted sources. These messages use social engineering techniques to create curiosity, a sense of urgency, or panic in the receiver and persuade them to take an unwanted action.
The rise of bring-your-own-device (BYOD) policies and remote work setups has resulted in more individuals using their mobile devices for work. However, this trend also creates vulnerabilities that cybercriminals can exploit to invade company networks through employees’ cell phones. It has provided an opportunity for smishing scams.
What are the types of smishing attacks?
Here are some common types of smishing attacks:
Customer support scams
Scammers might pretend to be customer support agents from trusted brands like Alibaba, Apple, or other reputable companies to deceive users. They often claim an issue with the victim’s account or promise an unclaimed reward or refund. They then direct victims to a fake website to steal their banking or credit card details.
Example of customer support scams:
URGENT: Your account has been compromised. Please click on the link below to verify your information and prevent any unauthorized access: [malicious link]. If you have any questions, contact our customer support immediately.
Fake job offers
You receive a text message claiming to offer a job opportunity with high pay and flexible hours. However, the job doesn’t exist, and scammers may ask for upfront fees, personal information, or bank details. They falsely present it as part of the hiring process.
Example of fake job offers:
Sender: XYZ Company HR
Message: Congratulations! You have been selected for a job at XYZ Company. Your skills and experience make you a perfect fit for our team. Please reply with your full name, date of birth, address, and bank account details for employment processing. Your first payment will be processed once we receive this information.
Government impersonation
You receive a text message claiming to be from a government agency, such as the IRS representatives or Social Security Administration, stating that there’s an issue with your taxes or benefits. The message asks you to click a link or call a number to resolve the problem, but it’s actually a scam to steal your personal information.
Example of government impersonation:
Sender: Department of Motor Vehicles (DMV)
Message: Your driver’s license renewal is overdue. Click the link to update your personal and financial information and avoid fines: [fake link]
Shipper impersonation
You receive a text message pretending to be from a shipping company like FedEx or UPS. The message informs you that your package delivery is delayed and asks you to click a link for more details. Clicking the link may create a fake website or install malware on your device.
Example of shipper impersonation:
Sender: FedEx Delivery
Message: Your package delivery is delayed. Click the link to track your package and reschedule delivery: [fake link]
Boss/Colleague scam
In this scenario, you receive a text message that appears to be from your boss or a colleague, asking you to urgently transfer money or provide sensitive company information. The message might create urgency or use authority to deceive you into taking action without verifying the legitimacy of the request.
Example of boss/colleague scam:
Sender: Steven Smith (Your Colleague)
Message: Hi [Your Name], can you send me the login credentials for the XYZ project? I need to access some files urgently. Please reply with the username and password. Thanks!
How does a smishing attack work?
Smishing attacks work by exploiting the trust and vulnerability of individuals through deceptive text messages. The attackers use social engineering tactics, such as creating a sense of urgency or fear, offering fake rewards or incentives, and using persuasive language to convince recipients to click on malicious links or disclose personal information.
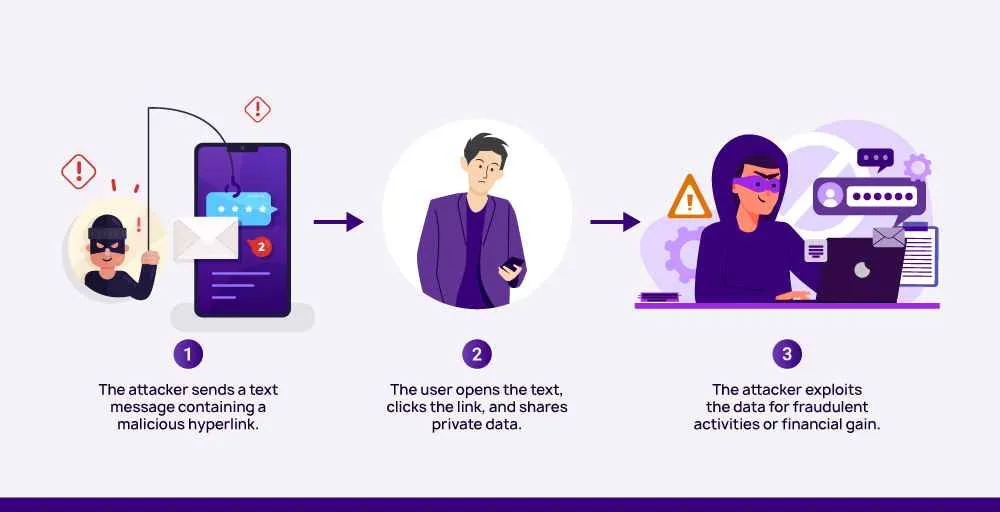
Here’s an overview of the typical process involved in a smishing attack.
1. Target identification: Attackers identify potential targets, often through mass messaging or targeting specific groups based on demographics or interests.
2. Developing convincing messages: Attackers craft text messages that appear legitimate and convincing. These messages often create a sense of urgency, fear, or excitement to prompt recipients to take immediate action.
3. Delivery channel: The smishing messages are sent via SMS (Short Message Service) to the target’s mobile device. They may also be sent through messaging apps, spoofing software, or other communication platforms.
4. Engagement tactics: The messages usually contain a call-to-action, such as clicking on a link, replying with personal information, or calling a phone number. Attackers may use various tactics to encourage engagement, such as offering fake rewards, threatening consequences, or posing as a trusted entity.
5. Data theft or malware: Once the recipient engages with the smishing message, they may be directed to a fake website or prompted to download a malicious app or file. This can lead to data theft, which involves the theft of personal information like passwords, credit card details, or social security numbers. Alternatively, malware may be installed on the device to allow attackers to gain unauthorized access or control.
How does smishing spread?
Smishing spreads through various methods, primarily via text messages or SMS (Short Message Service).
Here are some common ways in which smishing scams spread:
- Mass texting: Scammers send bulk text messages to many phone numbers, hoping some recipients will fall for the scam.
- Spoofed sender ID: Scammers can spoof the sender ID to make the message appear from a legitimate source, such as a bank, government agency, or well-known company.
- Phishing links: Text messages often contain links that direct recipients to fake websites to steal personal information, such as login credentials or credit card details.
- Social engineering attacks: Smishing scams often use social engineering tactics to manipulate recipients into trusting the message or believing it’s urgent and essential.
- Impersonation: Scammers may impersonate someone familiar to the recipient, such as a boss, colleague, or friend, to increase the chances of the recipient falling for the scam.
In 2017, the FBI found that Americans lost over $1.4 billion to cybercrime. A big part of that came from things like personal data leaks, identity theft, scams where people are tricked into sending money, and credit card fraud. So, it is crucial to prevent smishing attacks.
Smishing vs. Phishing vs. Vishing
Knowing the differences between Smishing, Phishing, and Vishing is important for staying safe and protecting against various cyber threats and attacks.
Some major differences are listed in the below table.
| Aspect | Smishing | Phishing | Vishing (Voice Phishing) |
| Definition | Smishing is a type of phishing attack that uses SMS or text messages to deceive individuals into providing personal or sensitive information. | Phishing is a cyberattack that involves sending fraudulent emails or messages to trick individuals into revealing sensitive information. | Vishing, short for “voice phishing” is a scam where cybercriminals use voice calls to impersonate legitimate entities and steal sensitive information. |
| Communication Medium | Smishing relies on text messages or SMS (Short Message Service) sent to mobile phones. | Phishing is primarily conducted through email but can also involve other forms like social media messages and harmful websites. | Vishing is carried out through voice calls, which can be traditional phone calls or VoIP services. |
| Immediate Action | Smishing messages often create a sense of urgency, prompting immediate action from the recipient. | Phishing emails may also create urgency, such as claiming a security breach or account suspension to prompt immediate response. | Vishing calls may pressure victims by creating urgent situations or threatening consequences for non-compliance. |
| Deceptive Content | Smishing messages use fake alerts or prize promises to trick people into responding or clicking malicious links. | Phishing emails use various tactics like fake login pages, urgent warnings, or offers to trick recipients into disclosing sensitive information. | Vishing calls may use impersonation tactics, claiming to be from banks, government agencies, or IT support to gain trust and information. |
| Delivery Speed | Smishing messages can be delivered quickly and reach many recipients simultaneously. | Phishing emails can also be sent to many targets simultaneously, allowing attackers to cast a wide net for potential victims. | Vishing calls are usually made in real time which allows attackers to adapt their tactics based on the victim’s responses. |
| Response Options | Recipients of smishing messages typically have limited options for response, usually either ignoring the message or reporting it as spam. | Phishing victims can ignore suspicious emails, report them, or verify the sender’s authenticity through other trusted channels. | Vishing victims may hang up, verify with the organization, or report the call to authorities. |
| Common Targets | Smishing attacks often target mobile phone users, especially those who use mobile banking or online payment services. | Phishing targets a wide range of users, including individuals, businesses, and organizations that use email for communication and transactions. | Vishing targets individuals who use telephones for communication, especially those who may be vulnerable to social engineering tactics. |
| Example | A text message claiming a prize or urgent issue, including a link to a fake site for stealing personal information. | A fake email from a bank asking for an account update. It then leads to a fraudulent website that steals login details. | A caller pretending to represent a trusted company or authority asks for personal information over the phone to steal data. |
| Prevention | Prevention measures for smishing include being cautious of spam messages, verifying sender information, and avoiding clicking on unknown links. | Preventing phishing involves education on spotting phishing attempts, using email filters, enabling multi-factor authentication, and verifying suspicious emails. | Preventing vishing involves being aware of spam calls, verifying caller identities through official channels, and avoid sharing sensitive information over the phone. |
How to identify smishing attacks?
Smishing messages can be harmful only if the recipient responds by clicking on links or sharing personal information with the attacker. However, you must identify smishing attacks to avoid falling victim to scams.
Here are some ways you can identify smishing and avoid becoming a victim of a smishing attack:
- Urgent messages demanding immediate action are a key sign of smishing attacks.
- Messages offering quick money, coupon codes, or prizes and requesting your personal information.
- Getting messages from people or numbers you don’t know (unknown senders) can be a sign of a smishing scam.
- Financial institutions never request sensitive information like credit card numbers or PINs via text or SMS.
- Be alert for mistakes in spelling or grammar in messages, as actual companies usually send messages with correct language and no errors.
- Storing banking information on a smartphone makes it a target for attackers. It’s advisable to avoid storing such sensitive data on a mobile device to prevent potential compromise in case of malware installation by attackers.
- If someone unexpectedly asks for personal information or money, don’t share anything or send money. Always verify their identity through official channels before taking any action.
- Report suspicious messages to your telecom provider or the FCC for investigation.
How to defend against smishing attacks?
You can defend against and prevent smishing attacks by combining technological, organizational, and individual actions.

Here are a few things to keep in mind to protect yourself against smishing attacks:
Individual solutions
- Avoid Clicking Suspicious Links: If you receive an unexpected or suspicious text, do not click on any links or download attachments.
- Be Skeptical: Always be cautious of unexpected messages, especially those requesting personal information or urging urgent action.
- Do not respond at all: You should not reply to text messages even if they request that you “text STOP” to end the message. You can delete all the suspicious text messages.
- Verify Contacts: If you receive a message claiming to be from a legitimate organization, verify the contact through official channels before responding.
- Never Share Your Personal Information: Avoid sharing personal, sensitive, or financial details over text unless you have started the conversation and are confident about the recipient’s identity.
- Be Updated: You need to stay informed about the latest smishing tactics and threats. Being aware can serve as your initial defense against such attacks. You should also regularly check and update your smart device’s operating system and security apps to the latest versions.
- Enable Two-Factor Authentication (2FA): You can use 2FA on accounts whenever possible to add an extra layer of security.
- Report Suspicious Messages: You should report suspicious messages to your mobile carrier and relevant authorities, such as the Federal Trade Commission (FTC) or the Federal Communications Commission (FCC).
- Register for A2P 10DLC Text Messaging: Your business can defend against smishing attacks by registering for A2P 10DLC text messaging. This service provides a verified sender ID, increases recipient trust, and includes compliance checks and opt-out options for enhanced security.
Technological solution
- Use security software: You can enhance your device’s security by installing and updating security software regularly. This includes antivirus and anti-phishing programs that can detect and block phishing attempts. Specific mobile security applications can also identify phishing links in text messages and stop users from accessing harmful websites.
- Multifactor authentication (MFA): It is a crucial security measure that adds an extra layer of protection even if attackers manage to obtain some credentials through smishing. It requires users to provide two or more verification factors to access their accounts, such as a password combined with a one-time code sent to their phone or email. This significantly reduces the risk of unauthorized access, even if login credentials are compromised.
- SMS filtering: It is a valuable tool available on many smartphones and through carriers. It helps users to identify and take action against suspicious texts. These filtering options can detect potential smishing messages based on various criteria, such as sender reputation, message content, and known scam patterns. Users can then choose to block, flag, or report these messages. It provides an additional layer of defense against smishing attacks.
Organizational solutions
- Employee training: Businesses can conduct regular training sessions to educate employees about smishing tactics, recognizing suspicious messages, and the importance of not clicking on links or providing sensitive information.
- Use secure communication channels: Organizations can encourage the use of secure communication channels, such as encrypted messaging apps or platforms, to reduce the risk of cybercriminals intercepting information.
- Collaborate with mobile carriers: Businesses can collaborate with mobile carriers to implement SMS filtering and block known smishing sources. It will help in reducing the risk of successful attacks.
- Reporting mechanism: Create effective channels for employees or stakeholders to report suspected smishing attacks. These reports help the organization issue alerts if a particular smishing campaign targets them.
What actions should you take if you become a victim of smishing?
If you become a victim of smishing, you can take these actions:
- Report the attack by contacting the institution or organization from which the message was claimed. This could be your bank or a service provider. Also, report the smishing attack to your mobile carrier and government officials like the Federal Communications Commission (FCC).
- Reset passwords and bank account PINs regularly whenever possible.
- Monitor your bank, credit card, and other financial accounts for unauthorized transactions and login locations. You can freeze your credit to block unauthorized use and protect against identity fraud.
- Update your mobile device’s security settings and enable two-factor authentication wherever possible.
- You can set up fraud alerts with Equifax, TransUnion, and Experian. This makes it harder for attackers to open accounts in your name.
- If you’re concerned about identity theft, consider signing up for an identity theft protection service.
- Run a system scan for viruses and malware, as scammers might place malicious software in your system.
- Learn how to detect and respond to smishing to avoid future attacks.
- Report suspicious or spam messages to 7726 (SPAM).
Wrapping up
Smishing is a dangerous tactic used by cybercriminals to steal personal and financial information, commit identity theft, and compromise security. It is crucial for you to stay alert and cautious when you receive unexpected or suspicious text messages. You should report any smishing attempts to relevant authorities, such as the institution mentioned in the message you get, your mobile carrier, and the Federal Communications Commission (FCC).
KrispCall, as a cloud telephony system, plays a crucial role in combating smishing. A2P 10DLC enhances SMS security by verifying sender information, monitoring message content, and offering opt-out options, effectively preventing smishing attacks. You can register A2P 10 DLC text messaging with KrispCall for secure and reliable SMS communications. This will significantly reduce the risk of users falling victim to smishing attacks.🌟
FAQs
What are the incentives behind attackers running smishing scams?
The incentives behind smishing attackers running scams are:
- Financial gain through selling stolen data or directly accessing bank accounts.
- Exploiting human psychology and trust to deceive victims.
- Access sensitive information for future attacks or to commit identity theft.
- Stealing sensitive information for identity theft.
- Redirecting payments to their accounts.
Is smishing an example of phishing?
Yes, smishing is a type of phishing attack. Phishing refers to the practice of sending deceptive messages (via email, text, or phone) to trick individuals into getting sensitive information or performing actions that benefit the attacker. Smishing specifically refers to phishing attacks conducted through SMS or text messages.