We have been able to simplify so many aspects of our lives with the development of the internet. With the myriad of tools available on the web, it’s very easy to communicate with a close friend or relative. Virtual phone numbers, often referred to as VoIP, are among the most amazing technologies available today to everyone.
But how safe is VoIP?
In the year 2017, telecom fraud accounted for 29.2 Billion where the most contributing losses came from PBX and toll fraud. This value has significantly dropped by 25% then as compared to the losses in 2015, so there is a temptation to think that this number indicates a decline in phone-based fraud, but it truly reflects consumers’ growing savviness about consumer fraud.
Hackers can cause severe damage to the bottom line of a business by stealing tens of thousands of dollars. Thanks to a few simple precautions, these fraud incidents that are persistent in the VOIP industry can be significantly reduced.
To prevent intrusions that rob you of money, time, and resources, for securing the primary settings on the devices such as routers, phones, etc.
What is VOIP hacking?
Hacking a VoIP number involves gaining access to its system by an unauthorized individual. A hacker can therefore listen in on all communications made by the number, the services that rely on it, and any sensitive information transmitted with it.
Hackers can also use VoIP numbers to rack up expenses. In some cases, these hacks are severe enough to bankrupt the firm. Additionally, hackers could impersonate your company to carry out fraudulent phishing activities.
Types of VOIP hacking
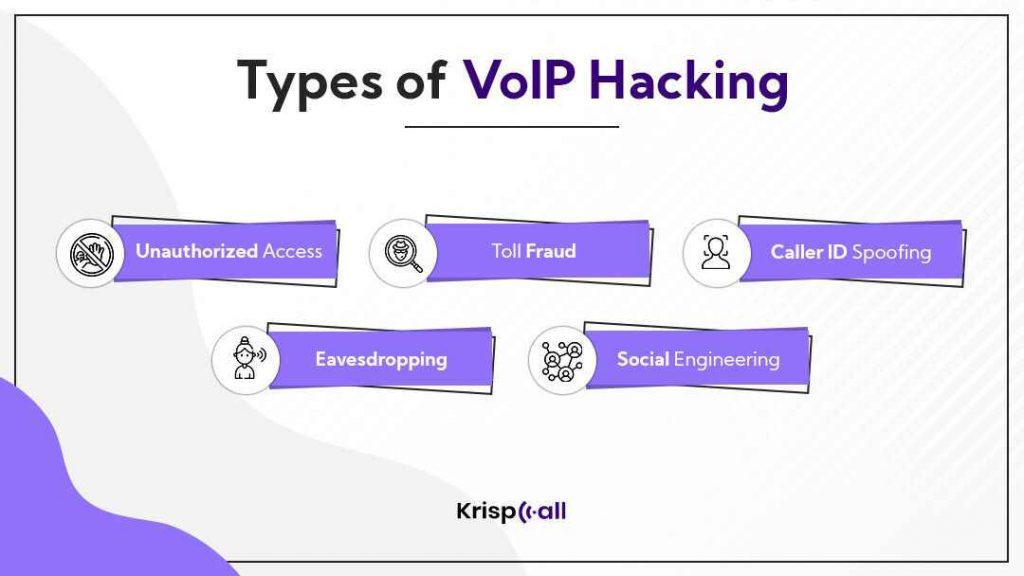
1. Unauthorized Access
A phone system attack involves hackers posing as you and calling other companies and people using the company’s phone network.
Hackers can get into your phone system and then make robocalls or use the auto-dialing programs without your knowledge.
The person who answers the phone placed from your caller ID on the other end might hear a pre-recorded message which asks for confidential information such as credit card numbers for the verification of their bank account. However, it isn’t you or your business that is making the call.
These techniques can also be used by hackers to access sensitive information. They can use your business phone service in this way to conduct fraudulent activities.
By impersonating your company, they can trick customers into revealing their private information.
How can it get any worse? When you set up your VoIP system yourself, you might be unable to detect the unauthorized pattern of calls made through your phone system.
You should thus check your call logs and history regularly and set alerts for when you exceed a certain threshold. By doing so, you’ll know about unauthorized use sooner rather than later.
2. Toll Fraud
The concept of toll fraud refers to the theft of long-distance minutes from a company’s VoIP network. A fraudster hacks a company’s PBX and then controls the hacked PBX to make long-distance calls. The fraudster will use hacked PBXs to complete long-distance calls to make money.
By using phishing scams, the attackers gain unauthorized access to your company’s VoIP system, which is targeted at administrators and system users.
A possible way for hackers to get access to your business is to leave a voicemail asking a department to confirm some details, such as bank account numbers.
If your employees identify themselves as hackers and pass the verification codes, such as IP addresses and phone system passwords, the criminals will gain access to your system. Hackers will then have access to large amounts of information they can use to hack your VoIP network and make expensive long-distance calls.
3. Caller ID Spoofing
In spoofing, communication appears to be from a known, trusted source even though it is indeed from an unknown source. Consequently, a caller ID spoofing scammer will manipulate the caller ID to trick audiences into believing the call is coming from a local or well-known number, helping them trust or answer the call.
When a call comes in from a particular name or number, your staff will usually respond. Thus, if the caller ID indicates that the call is coming from a trusted source, such as your VoIP provider, sensitive information may be exposed.
When you give that information, often without realizing it’s someone else, you’re opening the door for hackers to access your business’ VoIP system.
4. Eavesdropping
A literal definition of eavesdropping is to listen in secretly to someone else’s private conversations. Eavesdropping on VOIP communications refers to listening secretly to the conversation between two parties.
Nevertheless, eavesdropping can only occur in unencrypted connections, or when the local network is compromised. An insecure Wi-Fi network – without Transport Layer Security (TLS) and Real-time Transport Protocol (SRTP) – invites attackers to monitor the network.
Using eavesdropping, hackers are capable of gaining information about your company, customers, and others. What’s even worse is that they can obtain content from any recorded media.
5. Social engineering
Social engineering focuses on human interaction rather than technicalities in VoIP systems. In general, your staff likes being friendly and has no grounds to reject harmless requests, which might unknowingly provide attackers with information for future crimes.
Several factors contribute to the success of this hacking method, including poorly executed social engineering campaigns. It is rare for companies to tell their employees about the risk of fraudulent phone calls made by potential attackers using false caller IDs.
Criminals, on the other hand, use sneaky methods to obtain information about targets. By doing so, they might create a hostile environment that tempts staff to disclose sensitive information at the time.
How to identify if the VOIP system is under attack?
If you suspect your number may be compromised, you should be on the lookout for a few tell-tale signs:
- There may be incoming and outgoing calls in your phone history you do not remember, which could indicate someone has been making calls without your consent.
- Webcams and microphones are acting strangely. Using these devices is essential for making and receiving video and voice calls. You may be unaware that someone is controlling them from the internet without your knowledge if they suddenly start recording or turning on without your input.
- You have skyrocketing bills. As VoIP services are notoriously affordable, an extremely high number indicates a lot of calls on your bill. Accordingly, you should pay attention to your phone history.
- Suddenly, an antivirus message appears. An antivirus will normally send you a warning when it detects unusual activity on your device. An alarm might be triggered by unauthorized activity on the Internet by scammers and hackers. You may want to consider that your device may be under attack if these messages appear too often.
How to Stop VoIP Hacking?
A company’s VoIP system can be hacked in so many ways: the entire business could go offline, answerphone messages could be crude and offensive, voicemails can be deleted, calls to premium numbers can be made fraudulently at more than premium rates, intruders can listen in to private conversations, and customers’ calls can be routed to another number.
Upon reading that list, you might wonder why anyone would want to use a VoIP phone system. However, it is fact that typically, companies do not have to face such nightmarish scenarios, and by taking sensible measures, you can greatly reduce or even eliminate the risk of being hacked.
Following are some of the proven strategies that you can implement to prevent VOIP from being hacked:
Select the right service provider
VoIP phone security is heavily influenced by the VoIP service provider you choose. Because of this, you need to determine your security needs based on the sensitive nature of the information that will be exchanged through phone calls.
You should also find out what kinds of system precautions the provider has put in place to fend off attacks.
VoIP traffic tracking and notifications for suspected incidents or activities are key preventative measures that you should look for in a provider.
In light of this, you should investigate those providers who offer features tailored to your needs.
Control administrator access
A VoIP administrator has access to all of your business phone system’s administrative functions. This provides users with the ability to manage the bill, join conference calls, set up new lines, and lead to more costly intrusions.
Because it takes one fooled or bribed employee to allow hackers to attack your system, it is better to limit administrator access to fewer employees. By doing so, you reduce the chance of social engineering attacks.
While people commit mistakes, if they have lower-level permissions, the impact of the errors is minimized. Thus you should be extremely careful while you grant administrative access to the employee with your VOIP system.
Use VPN
If you or your team work remotely, use a virtual private network or a proxy. Oftentimes, data passing on the internet is unencrypted, making it vulnerable to man-in-the-middle attacks.
You can eliminate this problem by using a VPN or proxy service to enable a secure connection between you and your service.
Read Also: Top 7 VPN for VoIP Services
Analyze the call details
The easiest way to combat VoIP fraud is to analyze Call Detail Records (CDRs).
Providers of VoIP services should implement a system to detect fraud, PBX hacking, traffic spikes, and unusual call patterns.
They work best if the results are reported almost immediately. There should also be a mechanism to monitor the analysis, especially at night, on weekends, and holidays.
A good analysis solution will provide alerts or integrate with your routing system to block suspicious calls temporarily.
Use a strong password
When you install your VoIP solution, you are given a default password by the provider. You should change this password as soon as possible.
Additionally, you should teach your employees the best practices for strong passwords. The best way to prevent them from using simple or the most common passwords is to make sure they are aware of the dangers of using similar passwords for multiple accounts.
Additionally, passwords should be regularly changed to prevent team members who are no longer working with you from accessing the system and performing other malicious actions.
Use two-factor authentication
This method involves adding a security layer to your authentication process and is a proven technique in the industry.
You can use a security factor either that you know (a strong password or secret question), something you possess (your cell phone), or something you are (like using your face for authentication). Ideally, at least two security factors should be used.
Test your network
In many cases, small businesses set up their VoIP systems once and never look at them again. However, this leaves them vulnerable to a VoIP hack. It is possible that the setup you are using is less secure than it once was.
A regular network check will help you spot any security gaps in your VoIP system. It is important for administrators to regularly check access control and best practices.
Prepare a response plan in case a breach occurs
It doesn’t matter how well your company’s security measures are implemented, hackers can still crack them and get into your system.
Thus, you must have a detailed response plan in the event of a data breach. It should detail what your company will do if an attack occurs to prevent situations from getting worse if the company is in a state of confusion and does not know what to do.
Another crucial document is the disaster recovery plan. It details the steps to take to recover any data lost and mitigate the impact of any worst-case scenarios that may occur.
Summary
Fraudulent VoIP activities have been and will continue to be lucrative for criminals. It is likely that schemes to defeat the VoIP system will become more sophisticated and powerful as VoIP continues to grow in popularity.
The VoIP provider and enterprise must team up to ensure their networks are secure from all angles. VoIP providers can minimize their fraud risks by securing their networks and analyzing traffic for fraud signs.