Are you worried about your call center security 🔐?
Does your business still rely on outdated security methods?
In this fast-paced world, call centers may face the problem of protecting customer-sensitive data worried about data breaches, and implementing specific security solutions.
In this blog, you will cover everything we need to know about the best security practices in a call center, understand their importance, and identify the primary threats in this informative blog.
🔑KEY HIGHLIGHTS
- Call center security involves protecting the call center system from unauthorized access.
- Improve your security posture and protect consumer data with call center security.
- It may avoid expensive security breaches and win their customers’ confidence.
- Uses strong encryption for storing and transmitting data, both at rest and in transit.
- Train your employee about their system protection from malicious activity.
Let’s get started!
What is call center security?
Call center security is the process of protecting the system from unauthorized access to safeguard personal information and ensure its availability, confidentiality, and integrity in a call center environment.

Maintaining customer trust and safeguarding the reputations of the call center and the organization it serves.
Call center security example: A call center started losing their customer’s sensitive data because of cyberattacks, but then they started implementing call center security practices and then they started protecting their customer information.
Why is call center security important to call center business?
Call center security involves protecting the system from unauthorized data or access. Crucial elements include ensuring encrypted communication lines, safe authentication procedures, and ongoing worker training.
It is impossible to overstate the significance of contact center security because it not only keeps consumers safe from damage but also preserves the company’s trust and image.
It protects customer personal 👨 information from theft, such as name, location, phone number, and social security phone number.
It helps to prevent fraud and cybercrime.
What is the biggest threat to call center security?
The biggest threat to call center security is frequently associated with data breaches, social engineering assaults, and different types of call center fraud. Among them, some are explained below:

1. Internal threat
One significant risk comes from personnel who are malicious or who unintentionally compromise security. This may involve information theft, system disruption, or black market information sales.
2. External threat
External dangers originate from outside the company and might take the form of social engineering, hacking efforts, or cyberattacks. These attacks seek to get unauthorized access or interfere with regular business activities by focusing on infrastructure weaknesses in the contact center.
3. Data breaches
Call centers handle sensitive consumer data; they are often the focus of hackers looking to steal personal information, commit identity theft, or even use blackmail. Malware infecting systems and social engineering strategies deceiving agents into disclosing information are examples of attack types.
4. Phishing attack
Scams and phishing 🎣 emails aimed at contact center agents are frequent. Systems and data can be compromised by opening harmful links, downloading malware, or disclosing private information to callers that appear to be trustworthy.
Top 10 Practices for Call Center Security in 2024
Cyberattacks target call centers because they handle sensitive consumer data. Strong security procedures are more important than ever in 2024 due to the changing threat landscape and tighter laws. The following list contains the top 10 methods to keep your contact center safe:
1. Data encryption
Data encryption helps protect sensitive information by encrypting it into an unreadable format. Only the authorized person can access it.
To protect sensitive customer information during processing, transport, and storage, implement strong data encryption mechanisms to guarantee integrity and confidentiality.
KrispCall takes reasonable and practical precautions to protect your personal information. These precautions ensure that all data transferred over the websites is securely secured by utilizing HTTPS for encrypted data transfer.
calls made with KrispCall are encrypted during the transmission procedure from agents to KrispCall.
✅Do’s: Implement strong encryption algorithms and keys
❎Don’ts: Never use weak or outdated encryption algorithms
2. Access control
Strictly enforces access rules, allowing only authorized workers to access the system. In addition to preventing unwanted access, this guards against internal dangers.
Enforce a strong password for the system, and regularly review and update the permissions with multi-factor authentication.
KrispCall does not directly own access to the data that its clients gather from its clientele. A client may simply upload or save its customers’ information.
It is the responsibility of each client to inform its clients about the use and storage of their customers’ data.
✅Do’s: Grant the minimum level of access needed for users to perform their jobs.
❎ Don’ts: Avoid using generic accounts that multiple people can access.
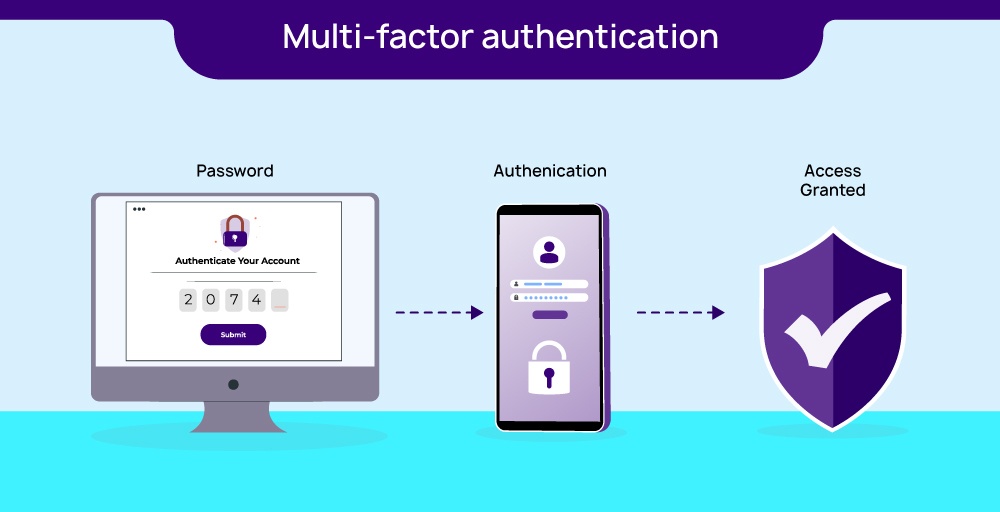
3. Multi-factor authentication
Using multi-factor authentication, you may strengthen your security measures by making users confirm their identity using more than one method, such as passwords and fingerprints.
A password, a security token, or biometric data are usually combined with something the user already knows or has. MFA improves authentication security and increases the difficulty of account penetration by unauthorized users.
✅Do’s: Put a common option that includes SMS codes, mobile authenticator apps, security tokens, and biometric verification.
❎Don’ts: Don’t Make MFA too complex or inconvenient this will cause user frustration and resistance.
4. Endpoint security
Endpoint security responsibilities include guarding against phishing and malware assaults, lowering the possibility of any outages, and dealing with insider threats from the contact center.
Call centers may strengthen their defenses, preserve data integrity, and have a strong security posture in the face of changing cybersecurity threats by giving endpoint security priority.
Putting safeguards in place to keep these devices safe from malware, phishing scams, and illegal access is known as endpoint security. By doing this, the network integrity of the call center is improved overall.
✅Do’s: Enforce firewalls to act as gatekeepers, filtering incoming and outgoing traffic to prevent unauthorized access and malicious activity.
❎ Don’ts: Never ignore software updates because delay in updates leaves your systems vulnerable to known exploits.
5. Password
Passwords must be strong and unique for every account. Do not repeat the same password for multiple accounts; it may damage your security.
Update your password from time to time. Do not keep the same password for a long time.
✅ Do’s: Set up Two-factor authentication and biometrics for every account
❎ Don’ts: Don’t share the same password with everyone,
6. Monitoring
Install continuous monitoring systems to minimize the effect of possible security events by quickly identifying and responding to suspicious activity.
Track activity within systems and networks, detect potential threats from the system and manage the possible security of the system.
Sturdy monitoring systems can spot irregularities or suspicious activity, which enables the company to react quickly to possible security issues.
✅Do’s: Choose appropriate tools and technologies to capture, analyze, and visualize the data you need. Centralized dashboards can provide a comprehensive overview of security posture.
❎ Don’ts: Never Ignore alerts when your failure to investigate security alerts promptly can leave your systems vulnerable and increase the risk of damages.
7. Voice authentication
By integrating voice authentication solutions, you may improve caller verification, increase security, and lower the possibility of identity-related fraud.
Verify identity by using unique voice characteristics and adding an extra layer of security for phone-based interactions.
Voice authentication systems use distinctive speech traits to make sure that only those with the proper authorization may access particular services or data.
✅Do’s: Collect high-quality voice samples during enrollment under controlled conditions, ensuring accurate future comparisons.
❎ Don’ts: Don’t rely solely on voice authentication. Layer it with multi-factor authentication, knowledge-based questions, and access controls for optimal security.
8. Regular software updates
Keep updating all systems and software with the most recent security updates. Updates regularly aid in patching holes and defending against new attacks.
Regularly updating your system can help protect your device from hidden threats or malicious activity.
Not only can software upgrades increase security, but they also boost the general functioning and speed of the system.

✅Do’s: Create backups of essential data and systems to enable recovery in case of any issues during the update process.
❎ Don’ts: Never deploy updates without thorough testing to prevent compatibility issues or system failures.
9. Secure payment processing
Adopt industry-compliant secure payment processing systems to guarantee the secure handling of private financial data during transactions. Uses tokenization or encryption to protect cardholder information
By putting in place secure payment processing methods, such as encryption and PCI DSS compliance, a business may better safeguard consumer payment information and foster confidence in its financial data handling practices.
✅Do’s: Implement fraud detection and prevention tools to analyze call patterns, IP addresses, and other factors to identify and block fraudulent transactions.
❎ Don’ts: Never store full credit card numbers or other sensitive data on agents’ devices or call center servers.
10. Vendor and third-party security
With the possibility of sensitive data disclosure, call centers must make sure vendor and third-party access is secure. Ensuring the security of this data is essential for fulfilling legal obligations and managing risks successfully.
To avoid potential weaknesses in the call center’s overall security posture, it is imperative to ensure the security of these external organizations. Companies should evaluate the security controls put in place by suppliers and set up explicit security guidelines for any partnerships with outside parties.
✅Do’s: Include clear security obligations in vendor contracts, outlining data protection responsibilities, breach notification requirements, and access controls.
❎ Don’ts: Don’t assume vendors automatically have robust security simply because they’re established.
How to train your employees about contact center security practices?
Take the following actions to train your employees on contact center safety procedures:

1. Set Clear Goals and Objectives
Provide a clear explanation of the training’s goals and expected results for your employees. This may include abilities like seeing security risks, managing sensitive data securely, spotting phishing scams, and security guidelines.
2. Create Interactive Training Resources
To keep your employees interested, mix educational and engaging materials. Utilize a variety of formats, such as role-playing exercises, video lessons, live sessions, e-learning modules, and quizzes.
Make the content relevant to potential real-world situations that they may run into. Make use of believable case studies and simulations to highlight effective practices and possible hazards.
3. Discuss important security topics
Cover all the important security topics, such as data security, access control, endpoint security, multiple factor authentication, social engineering, and phishing to employees of call centers.
These topics can help you learn about the security threats that can hamper your device, steal your personal information, and sell it to the black market.
4. Monitoring and Accountability
Establish mechanisms to track employees’ compliance with security procedures and ensure that they are followed. In the course of performance reviews, go over security procedures often.
Monitor every suspicious activity that can hamper your security regularly.
Secure Your Call Center Business with KrispCall Top Notch High Encryption Virtual Call Center Software
KrispCall is a call center service provider with VoIP services that encompass both single-level and multi-level auto-attendants. This VoIP solution is intended to save costs without sacrificing top-notch customer service.

KrispCall offers excellent automated services, including a dial-by-name directory and an easy-to-use phone tree editor.
Features
- Expand your global reach with KrispCall’s global calling feature and connect with customers worldwide.
- KrispCall’s intelligent call routing helps you connect with the proper person more quickly to improve customer satisfaction and quickly address concerns.
- Use Automatic Call Distribution systems to distribute incoming calls to the most appropriate agent.
- With KrispCall call monitoring features monitor live calls to ensure quality, provide coaching, and gather insights into customer interactions.
- Use KrispCall Integration with Customer Relationship Management (CRM) systems to allow agents to access customer information quickly during calls.
KrispCall benefits your business because it provides a VoIP feature with simple access to call center software on any device from anywhere. You can improve your call center’s performance, increase revenue, and increase customer satisfaction with KrispCall call centers.
Conclusion
Call center security goes into great detail on the important facets of contact center security, emphasizing their significance in protecting sensitive information and client confidence. It promotes strong security procedures and addresses both external and internal dangers, data breaches, and phishing attacks.
Clear objectives and interactive tools are emphasized in the staff training handbook. KrispCall, a VoIP service provider, encourages them to proactively advocate for increased security.
Connect with the KrispCall team to enhance the security of your call center with our expert advice on data protection.
FAQ
1. Should we use multi-factor authentication (MFA) for call center logins?
Yes, you should use multi-factor authentication for the call center login to secure the device.
2. Are there any helpful tools or resources for assessing and improving contact center security?
Yes, there are helpful tools or resources for assessing and improving contact center security.
3. What should we do in the event of a security breach?
Change the passwords for your account. If there are security questions and answers or PIN codes attached to the account, you should change these too in the case of a security breach.